
RSA Identity Governance and Lifecycle
Address Identity Risk and Act with Insight

Our Price: Request a Quote
Click here to jump to more pricing!
Please Note: All Prices are Inclusive of GST
Overview:
RSA Identity Governance and Lifecycle simplifies how access is governed and streamlines access requests and fulfillment. The solution helps you focus on what matters most to mitigate risk and maintain a continuous state of compliance.
RSA Identity Governance and Lifecycle delivers continuous access assurance for organizations to help ensure that users across the organization have the proper level of access. By providing visibility across your islands of identity in today’s blended cloud and on-premises environment, RSA Identity Governance and Lifecycle empowers business users to take action quickly and easily to address risky access situations with the highest business impact in order to reduce business risk and ensure compliance.
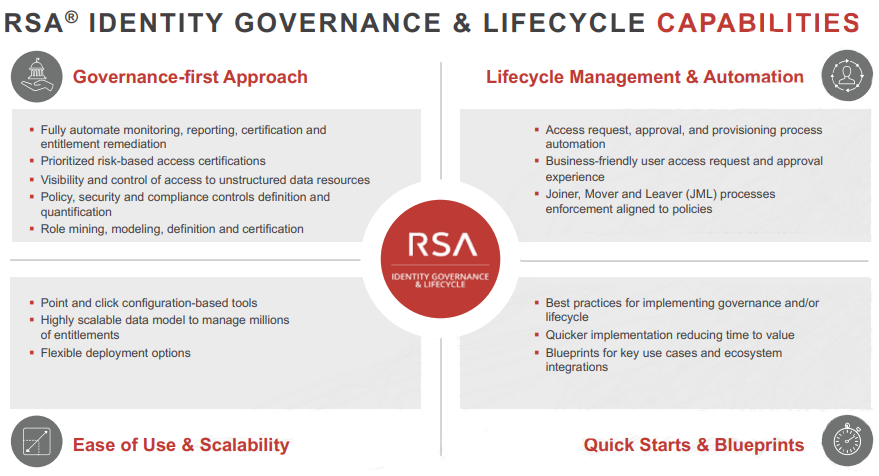
RSA Identity Governance and Lifecycle takes a governance-first approach to manage identity risk and ensure that the security posture of the organization is intact with regard to user access. This is accomplished by automating access review and certification processes for greater operational efficiency, cost and time savings, and by flagging issues between formal review campaigns. In addition, access certification responsibility and accountability are transferred to the people who understand access needs best-the business. Business-driven certification discourages access approval “rubber stamping.” Business users are provided with prioritized access issues based on risk informed by intelligence so they are empowered to take action with insight on what matters most.
- RSA Identity Governance and Lifecycle enables you to implement security and compliance controls (e.g., segregation of duties, unauthorised access permissions) to ensure policy and control objectives are met continuously
- To ensure users quickly gain access to the applications they need, RSA Identity Governance and Lifecycle provides the ability to grant access based on user roles and well-defined processes that enable the manager to provide access in a user-friendly way. It also manages entitlements (joiners, movers and leavers) across applications to ensure access stays current with users’ roles and that there is no overprivilege. The entire process of access request, approval and provisioning is automated using business-friendly language for approvals in order to ensure that users obtain appropriate access quickly
- Ease of Use and Scalability-In order to respond to ever-changing business needs and a dynamic threat landscape, RSA Identity Governance and Lifecycle provides security teams with the ability to configure and update policies, processes and controls quickly with point-and-click configuration tools that do not require customization and that provide quick time-to-value. In addition, high scalability allows your business to grow without needing to worry about the system, a critical factor given the number of applications and identities involved in business processes.
- Quick Starts and Blueprints-To ensure that your organization is managing identity risk effectively, we have recently introduced best practices and blueprints to provide a set of use cases and recommendations to allow you to speed your time-to-deployment and time-to-value.
Simplify governance of user access, automate provisioning and de-provisioning processes and ensure compliance with RSA Identity Governance & Lifecycle.
- Identity Governance
RSA Identity Governance helps organizations manage compliance on a consistent basis by fully automating the monitoring, reporting, certification and remediation of user entitlements. - Identity Lifecycle Management
RSA Identity Lifecycle helps to ensure the right people have the right access at the right time. The solution streamlines the access request and provisioning process for business users with an intuitive, self-service interface and an innovative approach to provisioning user access across all target systems. - Data Access Governance
RSA Data Access Governance provides IT organizations with the ability to monitor, report on and certify the legitimacy of user access permissions to unstructured data resources stored on Microsoft Windows, Linux and UNIX file servers; network-attached storage devices; and Microsoft SharePoint servers. - Role Management
RSA Business Role Manager delivers top-down and bottom-up role discovery, creation, modeling and suggestions. It helps streamline access based on "birthright" entitlements associated with specific functional roles so that, for example, HR managers receive access to HR systems. It also enables a metrics-driven approach to role modeling based on pattern analysis and policy validation.
Features:
![]()
Access Certification
Enable user-friendly access certifications by providing the business context and risk-based prioritization to business owners to complete more accurate and timely access reviews.
![]()
User Provisioning
Streamline and automate all phases of the user provisioning process, from request and fulfillment to de-provisioning as users join, move within or leave your organization.
![]()
Policy Automation
Automate access reviews and certifications to ensure all access is assessed against existing business policies and controls.
![]()
Self-Service Access Requests
An intuitive interface makes it easy for users to submit their own access requests and track approvals.
![]()
Advanced Reporting
Ad-hoc and built-in reports and dashboards provide a centralized summary analysis of access across all users, data resources, entitlements and certifications.
![]()
Role Management
Easily discover, create and model different roles based on “birthright” entitlements or other factors.
Benefits:
Simplify Access Governance
Fully automate the monitoring, reporting, certification and remediation of user entitlements to simplify access delivery and meet ongoing compliance demands.
Gain Control and Visibility
Improve your ability to safeguard data by quickly identifying orphaned accounts, inappropriate user access and policy violations with a unified view of access across all of your systems and applications.
Speed Deployment at Lower Cost
A configuration-over-customization approach helps reduce the time and cost it takes to get your identity governance solution up and running. The solution lowers ongoing maintenance costs, ultimately reducing overall time to value.
Streamline Fulfillment of Access Requests
Ensure your users gain access to the resources they need, when they need them, in accordance with compliance requirements.
Leverage Identity as an Enterprise Risk Control Factor
Provide risk and compliance teams with actionable data to identify the potential risks your employees, partners, customers and contractors pose. These insights can yield powerful compliance controls that reduce the risk of a breach or noncompliance.
Achieve a Sustainable Identity and Access Management Program
Enable users to quickly and easily connect to applications and empower administrators to easily manage policies, certification campaigns and system maintenance without costly customized coding.
Solutions:
Act with Insights
Identity has emerged as today’s most consequential threat vector. Without clear visibility and control over all identities and critical applications, organizations face increased vulnerabilities and potential compliance failures. RSA® Identity Governance and Lifecycle is designed to provide organizations the ability to act with insights to help make informed decisions with analytics to improve Identity Governance and Administration (IGA).
RSA Identity Governance and Lifecycle helps simplify how access is governed and streamlines access requests and fulfillment. With identity context across all applications, users, and policies, organizations can make decisions based on insights gleaned from what is happening in the business today to focus on what matters most to mitigate risk.
- Gain instant visibility into and control over who has access to what, and how they received it
- Manage all identities, including privileged access, in one place
- Make better informed decisions with near real-time insights versus static data points
- Prioritize security and compliance risks so you focus on what matters most
- Quickly answer the questions: What identity issues should I work on today? Where my risks? What are the recommendations to address them?
Deliver Business Agility
Business needs today require convenient solutions to ensure that business users have access to appropriate information to deliver against their objectives. RSA Identity Governance and Lifecycle simplifies how users request access to any resource, whether in the cloud or on-premises, and makes it easy for business owners to perform compliance tasks such as access reviews. When the business is empowered to achieve their goals, Information Security teams become valued partners.
- Ensure users conveniently receive appropriate and compliant access to the right resources to do their jobs-with an auditable trail
- Allow IT to align and support business objectives while maintaining the appropriate amount of control and compliance
- Meet business expectations and access SLAs with streamlined workflows and automation
- Reduce time to get up and running compared to traditional identity management solutions with configuration approach instead of one that requires extensive customization
Achieve a Sustainable Identity Access Management (IAM) Program
RSA Identity Governance and Lifecycle helps lower costs and boost operational efficiencies so organizations can achieve a sustainable IAM program.
With RSA Identity Governance and Lifecycle, staff can configure connections to applications and data, on-going policy administration, certification campaigns and system maintenance. All of this without costly customized coding means reduced costs to deploy and maintain as well as rapid time-to-value to deliver business results
- Attain more efficient operations at lower cost
- Develop and manage measureable and enforceable access policies
- Drive business adoption with interoperability with widely-used service desks like ServiceNow
- Achieve process optimization for governance and lifecycle
RSA Identity Governance and Lifecycle: A Phased Approach to Success
RSA Identity Governance
RSA Identity Governance simplifies how user access is governed across the enterprise. RSA Identity Governance makes it possible to achieve sustainable compliance by fully automating the monitoring, reporting, certification and remediation of user entitlements.
- Gain enterprise-wide visibility into all user access privileges and high risk applications
- Identify orphan accounts and inappropriate user access to reduce risk of audit failure and data breaches
- Transfer access certification responsibility and accountability to the people who understand access needs best-the business. Business-driven certification negates access approval “rubber stamping.”
- Automate access review and certification processes for greater operational efficiency, cost and time savings-flag issues between formal review campaigns
- Implement security and compliance controls (e.g., segregation of duties, privileged access, unauthorised access permissions) to ensure policy objectives are continuously met
RSA Identity Lifecycle
RSA Identity Lifecycle streamlines access request and fulfillment processes using business language to ensure users, both new and those changing roles, gain timely and appropriate access to the resources they need in accordance with compliance objectives.
- Automate and simplify the entire access request, approval, and provisioning process-in business-friendly language--to ensure users quickly obtain appropriate access without circumventing policy and process
- Automate request fulfillment and changes to significantly reduce the time, cost and effort of manual provisioning that expose the organization to access errors and audit failures
- Enforce Joiner, Mover and Leaver (JML) processes to reduce security and compliance risks
Privileged Access Management
Interoperability with CyberArk and Lieberman Software, leading Privileged Identity Management (PIM)/Privileged Access Management (PAM) suppliers, provides a centralized way to govern, manage and provision all privileged identities and their access entitlements. When RSA Identity Governance and a PIM/PAM solution work together, it brings all identity into one solution for easier management, enhanced audit performance and improved access assurance.
Identity Risk and Compliance Management
RSA Archer, is an industry leading governance, risk and compliance (GRC) platform and its interoperability with RSA Identity Governance and Lifecycle provides organizations a holistic and active risk view across applications, users and their entitlements to mitigate identity risk and automate identity compliance controls. Organizations can make access decision based on application risk.
- Bridge the gap between IAM and GRC
- Reduce enterprise risk
- Improve compliance posture
Complementary Add-Ons
RSA Data Access Governance
RSA Data Access Governance provides visibility, monitoring, certification and reporting of user access permissions to unstructured data resources stored on Microsoft Windows, Linux and UNIX file servers, network-attached storage devices and Microsoft SharePoint servers.
- Achieve visibility and control of who has access to unstructured data resources for greater protection of information assets and ease of compliance
- Meet new compliance requirements for data access while lowering costs associated with legacy or manual processes
- Establish closed-loop validation process for changes to data access permissions to more quickly detect out-of-band access that may indicate a security breach
RSA Business Role Manager
RSA Business Role Manager delivers top-down and bottom-up role discovery, creation, modeling and suggestion. RSA Business Role Manager helps streamline access based on ‘birthright’ entitlements associated with specific job roles (e.g., HR Managers receive access to HR system)
- Ensure more accurate and complete user governance and provisioning in accordance with Joiner, Mover, Leaver policies based on job roles
- Take a metrics-driven approach to role modeling based on pattern analysis and policy validation, resulting in a simplified process for collecting, assessing and analyzing established roles as well as defining new roles
- Achieve automated role certification, which ensures that business managers participate and buy in to role assignments
- Build a trusted system of record for reporting and analytics, enabling organizations to optimize roles by monitoring usage and effectiveness and track role changes for audit and compliance.
Extend the value of your RSA portfolio investments
Today’s solutions are being asked to solve bigger security challenges than originally intended. RSA Identity Governance and Lifecycle helps reduce identity risks with complementary RSA solutions to extend the value of your RSA investments.
Works with RSA SecurID Access to provide a complete, integrated Identity & Access Assurance solution that removes the need to tradeoff between convenience and security and eliminates “Islands of Identity”
Works with RSA Archer Suite for:
- Continuous monitoring of identity controls to reduce risk
- Appropriate access decisions based on application risk
- Improved incident response with business and identity context
Works with RSA NetWitness Suite to:
- Provide general identity context for the security analyst including access logs
- Make identity information available to better inform the investigative process
- Provide identity information to the behavior analytic engine as input data to discover risky user behavior
- Provide privileged user information to the security monitoring system
Documentation:
Download the RSA SecurID Suite Datasheet (.PDF)
Download the RSA Identity Governance & Lifecycle Datasheet (.PDF)
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing and product availability subject to change without notice.
Our Price: Request a Quote
Our Price: Request a Quote

