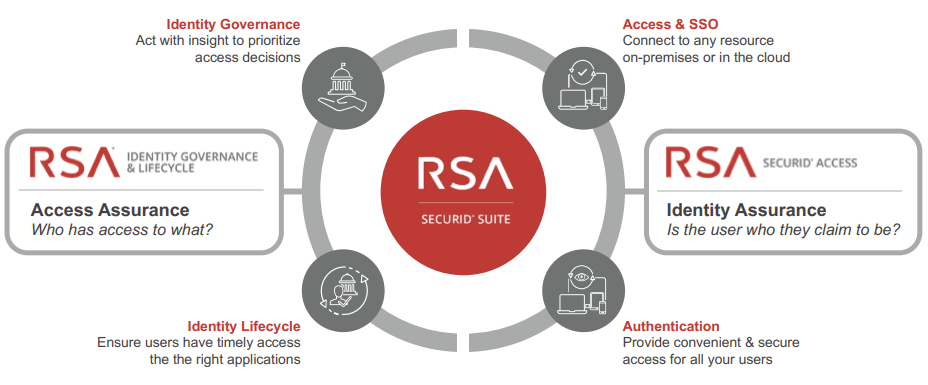
RSA SecurID Suite
Identity and Access Management
 Secure Access Transformed
Secure Access Transformed
Threats are multiplying. Users are changing. What are you doing?
Attackers are finding ways to compromise your users’ credentials every day. RSA SecurID Suite delivers the identity and access assurance you need to thwart them at every turn-while delivering an absolutely seamless access experience for your users.
RSA SecurID Suite goes beyond traditional identity and access management, using identity insights, threat intelligence and business context to provide secure access to all of your users, across all of your applications, from the ground to the cloud. It brings together multi-factor authentication, risk-based access management, identity governance and user lifecycle management in one powerful suite of solutions.
What Is Identity and Access Management?
Identity and access management systems safeguard critical applications and other resources by providing assurance that the people seeking access to them really are who they claim to be (identity management) and that they’re authorised to use specific resources (access management). In an era when applications are as likely to be in the cloud as on premises, and users are as eager to access them from mobile devices as desktops, successful identity and access management demands more than passwords. It requires analytics-driven insights into identities, a keen awareness of cyber threats, and business context to prioritize identity risks and protect assets accordingly.
The security and control to keep ahead of growing threats
The convenient access to stay in step with today's users
RSA SecurID Access
Protect critical resources with risk-based multi-factor authentication. RSA SecurID Access addresses a variety of user needs with a broad range of authentication methods including push notification, biometrics, OTP, SMS and tokens.
- RSA Authentication Manager
- RSA Software Authenticators
- RSA SecurID 700 Authenticator
- RSA SecurID 800 Authenticator
- RSA SecurID Appliance
RSA Identity Governance & Lifecycle
Make it easier to govern access with an automated approach that simplifies access approvals and certifications, speeds provisioning and deprovisioning, and provides complete control over who has access to what.
Benefits
Confirms users are who they say they are and that they have appropriate access for their roles.
Considers identity risk and business context for granting access or requiring step-up authentication.
Strengthens access protection across traditional, web, mobile and SaaS applications.
Brings the latest innovations to the world's most widely trusted multi-factor authentication solution.
Makes authentication frictionless for users and governance easy for administrators.
Convenient
Today’s users expect fast, convenient access to the data and applications they need to do their jobs. At the same time, IT needs an easy and effective way to protect anywhere-anytime-any device access to these assets that reside onpremises or in the cloud.
As a result, access controls must be secure, convenient and easy to deploy.
Easy for your business users
Your users need to access applications and information with minimal friction. Additional authentication should be used only when required. When additional authentication is needed, users should have a broad variety of modern, convenient multi-factor authentication options that provide stronger authentication for a variety of access cases and diverse set of users including employees, contractors, help desk, partners and customers.
Another key element of convenience is empowering business users to make access and authentication decisions and react to risky situations with a simple-to-use interface.
Easy for your IT staff
It is important to make secure access deployment and management convenient for IT so they can respond rapidly to business needs and strengthen and extend access-compliant protection across traditional, web, mobile and SaaS applications:
- Flexible deployment options, with the ability to respond to business needs quickly through easy onboarding of new applications
- Quick configuration options to optimize access decisions to respond to changing business needs and regulatory requirements
Intelligent
Intelligent authentication provides the benefit of reducing friction and adding security to protect applications and data that are critical to the business. It provides both security and convenience, and takes into account the needs of the modern workforce.
The intelligent approach to authentication considers the business context, or the impact of rogue access to an application on the business, to determine the policy or the required level of confidence needed to provide access to the application.
Identity assurance enables the organization to have confidence that users are who they claim to be. That assurance is evaluated at the time of access based on what the organization already knows about the user (e.g., a known device, user login information) as well as any risk indicators (e.g., login from a new location). Together, these determine a current level of confidence and drive the required levels of authentication to provide the appropriate level of identity assurance.
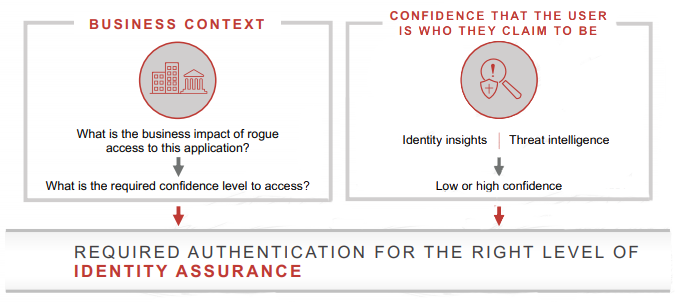
Intelligent access-When it comes to access control, the driver traditionally has been IT efficiency and streamlined provisioning of access to applications. But as organizations move to mobile and cloud technologies, it is critical to first gain a perspective on identity risk (for instance, the organization’s current state of access, and how to stop inappropriate/unauthorised access). To minimize access risk of an application or data, an intelligent approach to access decisions considers the business context and impact of rogue access to an application on the business, in addition to evaluating current risk based on a set of defined criteria (e.g., number of orphaned accounts and overprivileged users).
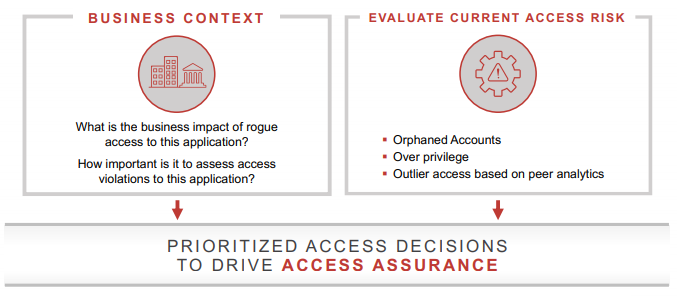
The combined intelligent perspective and risk-based approach enable the organization to prioritize access decisions based on what matters most and to drive the right levels of identity assurance-the confidence that the right people have access-and access assurance-the confidence that the access is appropriate for the user’s role/job and that the access is in compliance with corporate and regulatory policies.
Pervasive
Finally, a holistic identity solution needs to be pervasive and cover all access use cases. If a solution is good only for protecting a SaaS application or only an on-premises application and is not holistic across all use cases, an organization cannot achieve true identity and access assurance.
The reality is that with multiple sources of applications and data, user stores and identities will be scattered and decentralized. The goal is to connect to all of these “islands of identity” for unified visibility and control across all the access use cases.
By connecting to all applications, knowing who has access and having confidence that users are who they say they are at the time of access, organizations can apply a holistic approach to addressing the identity challenges of digital transformation.
With risk-based, multi-factor authentication, intelligent identity governance, and automated user lifecycle management, RSA delivers unprecedented identity and access assurance across all of your islands of identity-from ground to cloud.
Convenient, secure access for the modern workforce from ground to cloud
RSA SecurID Suite consists of two solutions that work together to address the security challenges of delivering access to a dynamic user population across complex environments.